Adam Gowdiak (Founder/CEO, Security Explorations)
PRESENTATION TITLE: Security Vulnerabilities of Digital Video Broadcast Chipsets
PRESENTATION ABSTRACT:
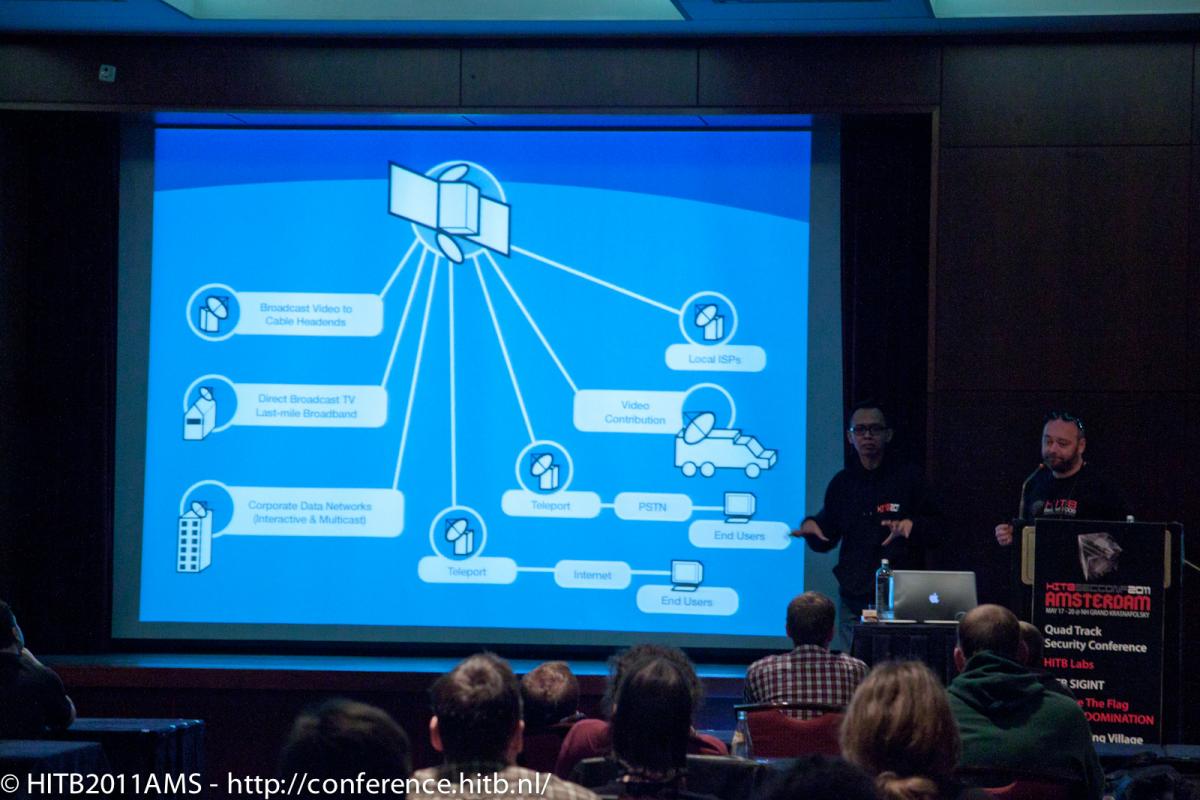
This talk will be a continuation of our presentation Security Threats in the World of Digital Satellite Television. In this talk we will however solely focus on the security of audio and video MPEG streams broadcasted to subscribers via their set-top-boxes by a digital satellite TV provider.
We will discuss in detail the security mechanisms such as Conax conditional access system with chipset pairing that is used by modern digital satellite TV set-top-boxes to protect against set-top-box hijacking and illegal sharing / distribution of a premium satellite TV content (TV channels and Video on Demand movies).
We will demonstrate the process of discovering the inner workings of a silicon chip implementing advanced DVB functionality related to the MPEG streams decoding and decryption. We will show the process of reverse engineering the instruction set of a completely unknown processor core embedded inside a DVB chip along with the steps that lead to the discovery of security vulnerabilities in a chip’s design / implementation. Sample exploitation scenarios of discovered security issues will be also discussed for the purpose of illustrating what real threat security flaws in DVB chipsets can pose for digital satellite TV operators and content providers.
More information about the topic of this presentation can be found at: http://www.security-explorations.com/en/SE-2011-01.html
ABOUT ADAM GOWDIAK
Adam Gowdiak is the founder and CEO of Security Explorations, a security start-up company from Poland which provides various services in the area of security and vulnerability research.
Prior to founding Security Explorations, he worked for the Poznan Supercomputing and Networking Center and Sun Microsystems Laboratories. For over 8 years, he had been also an active member of a notable Polish security research group called the Last Stage of Delirium or LSD.
Adam is an experienced Java Virtual Machine hacker, with over 50 security issues uncovered in Java technology over the recent years. He is also the hacking contest co-winner and the man who has put Microsoft Windows to its knees (vide MS03-026) and was also the first one to present a successful and widespread attack against the mobile Java platform in 2004